Configure SSO with Okta
This guide is intended for Admins setting up SSO SAML with Okta.
When you configure Single Sign-on (SSO) with Okta, your users will be able to create and sign into their Baserow accounts using Okta.
If you are looking for information on setting up SSO with other providers:
- Configure Azure AD for SAML SSO
- Configure OneLogin for SAML SSO
- Configure Google for OAuth 2 SSO
- Configure Facebook for OAuth 2 SSO
- Configure GitHub for OAuth 2 SSO
- Configure GitLab for OAuth 2 SSO
- Configure OpenID Connect for OAuth 2 SSO
Single Sign-On feature is a part of the Baserow Enterprise offering. Instance-wide features are only available on the self-hosted Enterprise plan. To learn more about the Baserow enterprise plan, visit our pricing page.
Here’s how to set up Okta to sign in to your Baserow account.
Set up SSO SAML with OneLogin
To get started, log into your Okta account and click Admin in the top right corner:

Click the Applications tab in the sidebar on the Okta admin page, then select the Applications option from the dropdown menu.
Next, click the Create App Integration button on the Applications page:

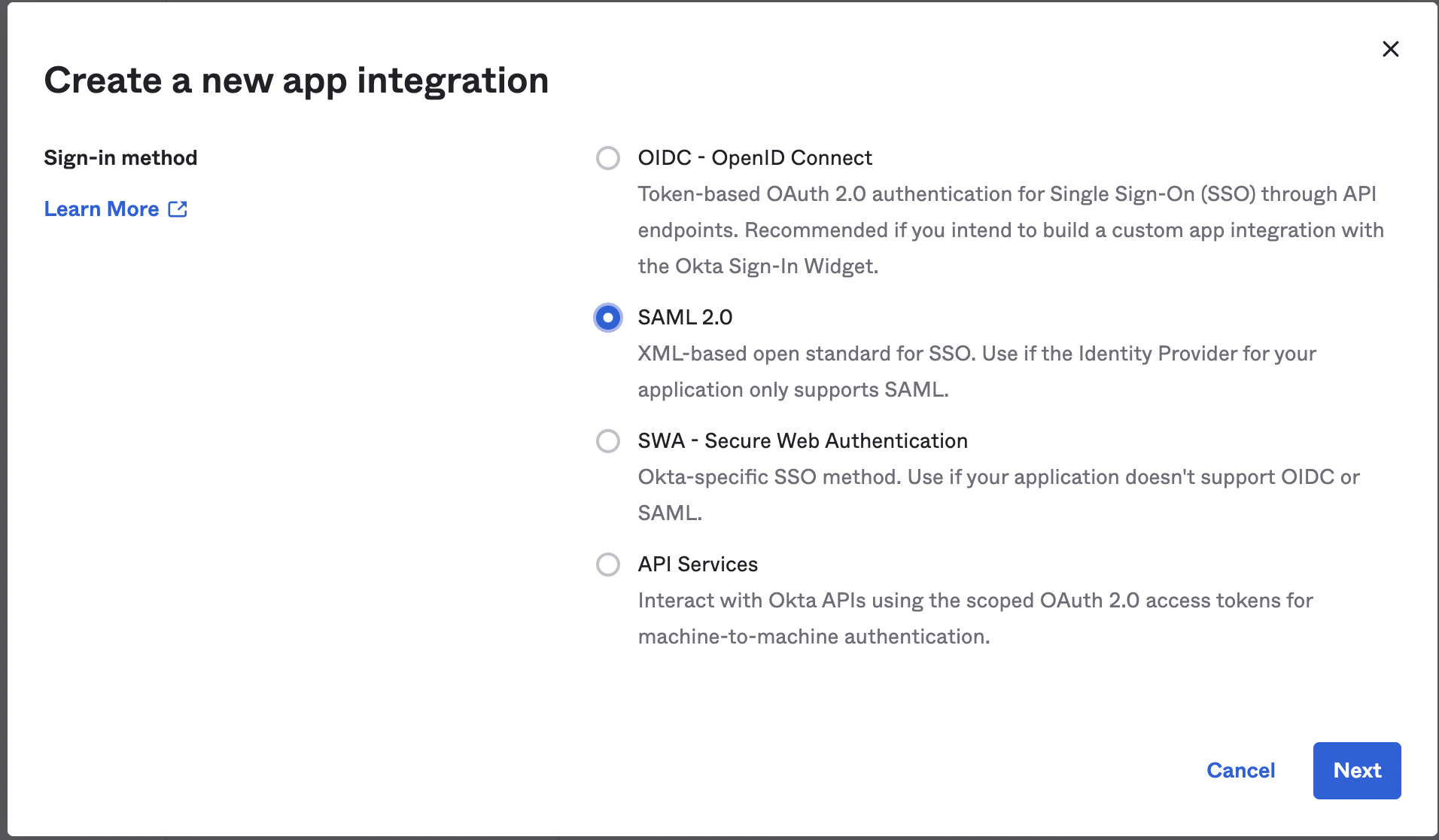
Choose SAML 2.0 as the sign-in method:
Choose Baserow as the app name and upload the logo for the application:

Next, retrieve your Default Relay State URL and Single Sign On URL from the admin settings modal in Baserow, following the steps in this guide.
To Configure SAML in Okta, add your Single Sign On URL in the first two fields (”Single sign on URL” and “Audience URI (SP Entity ID)”).
Add your Default Relay State URL in the “Default Relay State” field.
Create 3 attribute statements with values as such:
| Field name | Value |
|---|---|
| user.email | user.email |
| user.first_name | user.firstName |
| user.last_name | user.lastName |
Set all other fields like in the image below:

Click ‘Next’ to complete the configuration.
Once the app has been created, assign it to people from the ‘Assignments’ tab of the Baserow Okta application. This permits these people to send the user information from Okta to Baserow to create/log in to the account.

To ensure that the sign in works properly on Baserow, set the email domain associated with this app and paste the Identity provider metadata into Baserow.
The metadata can be found in the ‘Sign On’ tab. Scroll to “SAML Signing Certificates” section and then choose a certificate type with active status. From the actions dropdown of the active certificate, click “View IdP metadata”.

After you’ve accessed the information from the IdP Metadata, copy and paste the information from Okta into Baserow.
Connect Okta to your Baserow Account
Head back to Baserow Admin > Authentication > Provider.
Configure OneLogin by inputting the domain and metadata information into the corresponding fields in your Baserow Admin Dashboard, following the steps in this guide.
You should be able to log in with OneLogin after completing these steps by visiting your Baserow server login page. Your users will now be taken to a OneLogin sign-in flow when they attempt to log into Baserow. After logging in with their OneLogin credentials, they will be redirected to the app.

Understanding Baserow’s authentication system
By default, Baserow restricts users to logging in only with the same authentication method they used for signing up. For instance, if a user creates an account with a username and password, they won’t be able to log in through SSO without further configuration.
Troubleshooting error for SSO Login
You might encounter an error message — “Something went wrong: please use the provider that you originally signed up with” — when you attempt to log in via SSO.
This error message indicates a conflict between your initial sign-up method and your attempt to log in via SSO after initially signing up for Baserow with a username and password.
Here are the primary options to address this error:
Option 1: Enable multiple authentication methods
Set the environment variable BASEROW_ALLOW_MULTIPLE_SSO_PROVIDERS_FOR_SAME_ACCOUNT=true. After setting this variable, restart the Airtable instance. This allows users to log in with either a password or SSO.
This option increases security risk, especially if you have multiple OAuth providers enabled. An attacker who gains access to a user’s account on any external provider could potentially use that access to log in to the associated Baserow account.
For optimal security, we recommend maintaining consistent authentication methods unless necessary. If enabling multiple login methods is essential, implement additional security measures to mitigate potential risks.
Option 2: Maintain consistent authentication method
Users can continue logging in with the authentication method they signed up with. This avoids changing Baserow’s default behavior and maintains existing security measures.
Option 3: Delete user from Admin panel and re-login via SSO
You can delete the user from the Baserow admin panel. Upon logging in via SSO, Baserow will recreate the user, automatically setting SSO as their default authentication method.
Deleting the user permanently removes all their associated data within Baserow. This option should only be considered if data loss is acceptable and after ensuring all data is backed up elsewhere.
Always prioritize data security when modifying your authentication settings.
Related content
- Single Sign On (SSO) overview.
- Baserow Enterprise plan.
- Enable SSO in the admin panel.
- Email and password authentication.
Still need help? If you’re looking for something else, please feel free to make recommendations or ask us questions—we’re ready to assist you.
Contact support for questions about Baserow or help with your account.
